Written by: Lawrence Chin, Security Architect, Palo Alto Networks
The adoption of multi-cloud by the financial services industry (FSI) further cements the internet as a business enabler. Not that long ago, the FSI was leery of the internet for business use. Today, the internet is a vehicle for online banking, business to business (B2B) connections, software-as-a-service (SaaS), e.g., email, calendaring, customer relationship management (CRM), and public cloud. Financial institutions continue to make more assets and resources available on the internet for their customers and partners. The convenience of assets being available anywhere, anytime has become expected in today’s on-demand, instant gratification mindset.
Internet Dependency
As more corporate resources are internet-accessible and/or cloud-hosted, one implication is that remote campuses and branch offices have a strong reliance on the internet. Instead of backhauling this traffic through the corporate data center, financial institutions have adopted direct internet access from these remote sites to optimize the end-user experience. Moreover, the internet is used as an alternative to traditional wide area networking (WAN) technologies, e.g., multi-protocol label switching (MPLS).
The ubiquity of the internet is both a blessing and a curse. As a near-universal medium that provides access to resources worldwide, it is unparalleled. On the other hand, its wide availability makes it easily deployed by anyone in an organization and just about anywhere – with or without the involvement of information security or information technology (IT) teams. For example, a branch office can independently install a broadband internet connection for the convenience of their top producing financial consultant(s).
Ultimately, the value of the internet and its ready availability have made it difficult for financial institutions to inventory and manage all of these connections centrally. More than just a gap in the inventory, each untracked internet connection is a potential point of exposure for financial institutions.
Limitations of Internet Inventories
Digital asset sprawl has reached a point where an organization’s security department is unable to keep up with internet asset discovery, inventory, and management activities manually. It is a major challenge to obtain the visibility needed to effectively manage everything that is externally accessible. When portions of the network perimeter are unaccounted for, maintaining the security posture of the financial institution is daunting since routine measures such as penetration testing, vulnerability scanning, and patch management cannot always be thoroughly applied. This gap in the management of internet attack surfaces creates a significant amount of risk that financial institutions are not equipped to address.
When the internet was only accessible by traditional telecommunications facilities, a corporate IT department could easily manage and account for the few connections implemented at the financial institution. A spreadsheet could adequately capture all the relevant information (e.g., registered IP address ranges, domain names, and autonomous system numbers) about each internet touch point. This “golden source” would also satisfy the needs of the information security team to arrange appropriate protections for and monitor the internet-facing environments.
As mergers occurred, corporate IT organizations would share their respective internet inventory spreadsheets for appropriate due diligence and recordkeeping. Consolidation of these spreadsheets was a manual and error-prone process, yet it was the best available option. However, unknown and “rogue” internet assets would remain unaccounted for even during this well-intentioned data exchange.
Some financial institutions then resorted to self-assessments and scans based on information from domain name registries and WHOIS databases to discover any unknown internet assets. Others have enlisted third-party tools and/or security risk scoring services to fill the void. In many cases, these approaches have proven to be more resource-intensive to operationalize than originally imagined while still leaving many questions unanswered over false positives and misattributions. With incomplete or inaccurate internet inventories, financial institutions cannot thoroughly protect this critical asset class.
Exposed Internet Assets
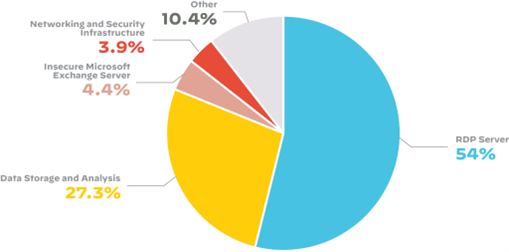
Figure 1: Distribution of risks across the financial services industry attack surface
As companies migrate more data resources and applications to the cloud and other internet-hosted environments, their attack surface grows accordingly. Advancements in scanning technologies allow threat actors to locate attack vectors quickly and easily. They can discover abandoned, rogue, or misconfigured assets that can become backdoors for compromise in short order. It has been reported that 69% of organizations have experienced a cyber incident resulting from an unknown, unmanaged, or poorly managed internet-facing device.[1] Consequently, it is important to understand what has been left exposed and the risk they represent.
To this end, the 2022 Cortex Xpanse Attack Surface Threat Report shows that Remote Desktop Protocol (RDP) servers account for 54% of the internet-visible resources among financial institutions. This is unfortunate as RDP is known to be a popular initial attack vector. Data storage and analysis systems are the next most exposed asset type in financial services. (See Figure 1.)
Attack Surface Management
A critical step to informing any risk management function is to have a clear understanding of one’s attack surface. To state the obvious, you can’t protect what you can’t see. To address this blind spot, financial institutions need a continuous, real-time, and regularly updated view of their attack surface. This allows them to discover, evaluate, and ultimately mitigate exposures of their known and unknown internet-accessible assets.
Attack surface management (ASM) provides continuous discovery, monitoring, and assessment of a financial institution’s internet-facing resources. The use of ASM discovery tools has found that the attack surface is at least 40% greater than originally perceived.[2] Left unaddressed, those unknown assets are easy targets for threat actors and create significant risks for financial institutions.
To address this issue, financial institutions can leverage ASM to create a single source of truth for all their internet-connected assets and their potential exposure to attacks – irrespective of being on-premises or spread across multiple cloud providers. In light of the growing dependency on the internet, a sound ASM strategy should be considered a fundamental component of cyber hygiene as financial institutions look to increase security maturity and reduce risk.
About the Author
Lawrence Chin
Security Architect
lachin@paloaltonetworks.com
About Palo Alto Networks
Palo Alto Networks is the world’s cybersecurity leader. We innovate to outpace cyberthreats, so organizations can embrace technology with confidence. We provide next-gen cybersecurity to thousands of customers globally, across all sectors. Our best-in-class cybersecurity platforms and services are backed by industry-leading threat intelligence and strengthened by state-of-the-art automation. Whether deploying our products to enable the Zero Trust Enterprise, responding to a security incident, or partnering to deliver better security outcomes through a world-class partner ecosystem, we’re committed to helping ensure each day is safer than the one before. It’s what makes us the cybersecurity partner of choice.
[1] “Security Hygiene and Posture Management,” ESG Research, January 2022.
[2] “Value Drivers for an Attack Surface Management (ASM) Program,” ESG, April 2022.