Written by Cheryl Chiodi
For financial institutions, obtaining executive support for cybersecurity programs can be challenging. Until there is an attack, executives rarely see the tangible benefit of funding an adequate program. According the latest EY and Institute of International Finance (IIF) bank risk management survey, 58% of Chief Risk Officers cite their financial institution’s inability to manage cybersecurity risks as their top strategic threat. Clearly, waiting for an attack to occur is a dangerous and shortsighted approach, as financial institutions are increasingly becoming targets for cybercriminals, and cybersecurity threats are constantly evolving, becoming more complex.
Figure 1 presents the top targets for phishing attacks, with financial services leading the pack.
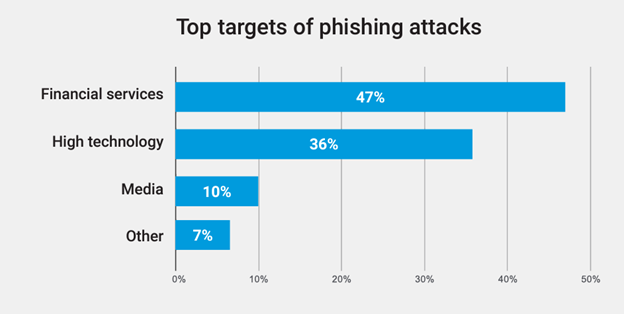
Figure 1 – Top targets of phishing attacks. Source: Akamai State of the Internet, Volume 8, Issue 3, Enemy at the Gates: Analyzing Attacks on Financial Services (https://www.akamai.com/resources/state-of-the-internet/enemy-at-the-gates-analyzing-attacks-on-financial-services)
To ensure a proper level of investment is made in the prevention, detection and mitigation of cyber threats, the board must understand the business benefits and the value of security as a strategic investment rather than just an operational cost. Here are five of the top tangible business benefits guaranteed to get the board’s attention:
Reducing the risk of data breaches
As financial institutions embrace digital transformation, their environments will become more complex and will include multi-cloud environments, containers, and third-party vendors. Security teams must be a part of digital transformation efforts. Without a security mindset built in, there is increased risk of vulnerabilities to cyberattacks, data breaches, and other security incidents. This can result in the loss of sensitive customer data, financial losses, and reputational damage.
Improving regulatory compliance
Financial services organizations are subject to numerous regulatory requirements regarding data privacy and security. Financial institutions will be required to submit reports to regulators after experiencing a significant service disruption, network intrusion, or unauthorized access to sensitive information. In some cases, there is also an obligation to report to regulators if a ransom is paid. Without a focus on security at the board level, organizations may struggle to meet these requirements, resulting in fines and other penalties. Regulatory compliance is also an important audit issue.
Risk mitigation
Cybersecurity risks can pose significant threats to the financial stability and reputation of a company. By prioritizing cybersecurity at the board level, financial services institutions can help to protect their customers, stakeholders, and the broader financial ecosystem from cyber threats.
Improved operational efficiency
Prioritizing cybersecurity programs ensures that the necessary resources, such as budget, personnel, and technology, are allocated to the cybersecurity program early. Addressing security incidents after they occur can be costly and time-consuming. Without a focus on security at the board level, financial services institutions may find themselves spending more on remediation efforts and incident response than on preventative resources.
Competitive advantage
Customers in the financial services industry are particularly sensitive to security and privacy concerns. If security is not a priority, customers may lose trust in the organization, resulting in a loss of business. Financial institutions must do a better job at protecting their customers, employees, and business operations from the ever-increasing threat of cyberattacks.
It’s important to convey to the board that cybersecurity can no longer be considered another line item that’s simply part of doing business. An effective cybersecurity strategy is a growth strategy, a priority launch pad for innovation, and a point of differentiation from the competition. While there’s no way to be completely protected against cyberattacks, promoting a culture of security within the organization, starting at the board level, shows a commitment to your customers, their data, and your reputation.
Cheryl Chiodi is Akamai’s Industry Strategist for Financial Services.
About Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away. Learn more about Akamai’s security, compute, and delivery solutions at akamai.com and akamai.com/blog, or follow Akamai Technologies on Twitter and LinkedIn.

